Forwarding Syslog Messages to Loki via Promtail and syslog-ng with mTLS
The Problem I recently set up Loki and Promtail in my Kubernetes cluster, which does a great job and finding any logs pushed to stdout just by using the default service discovery from the helm chart. However I’m also running an opnsense router, and I wanted to be able to ingest logs from it as well. Of course, I don’t want plaintext transmissions of my logs, nor do I want logs to be ingested from unauthenticated sources. Since already use a HashiCorp Vault server with a PKI engine enabled, I figured mTLS (mutual TLS) was the way to go. I...
Copying and Linux Permissions
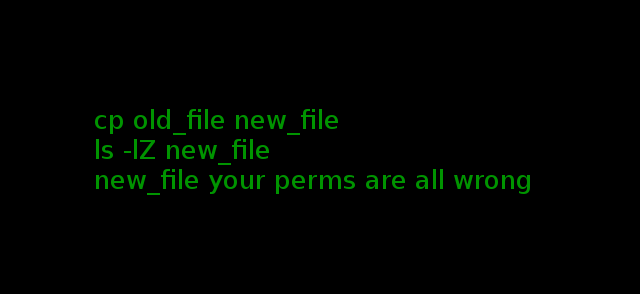 Last time I wrote about using the --reference flag for quickly replicating various aspects of permissions in Linux. Today’s post is how to copy files and retain various attributes, like permissions, ownership, and SELinux context. First, a little background on how permissions are set when copying. How Permissions are Set When Moving Files Or Why the Heck Do Permissions Change with Copying?! So you’ve noticed that when using the mv command permissions will stay the same, but using cp changes then. What’s going on here? Turns out this actually makes a lot of sense. In *nix, permissions are set based...
Last time I wrote about using the --reference flag for quickly replicating various aspects of permissions in Linux. Today’s post is how to copy files and retain various attributes, like permissions, ownership, and SELinux context. First, a little background on how permissions are set when copying. How Permissions are Set When Moving Files Or Why the Heck Do Permissions Change with Copying?! So you’ve noticed that when using the mv command permissions will stay the same, but using cp changes then. What’s going on here? Turns out this actually makes a lot of sense. In *nix, permissions are set based...
Cloning Linux Permissions
 Ever have that moment where you’re working on your SELinux enabled webserver and you’ve put in a fancy new file into /var/www/html and the darn thing just won’t show up properly, even though everything else is working? Then that sinking realization that you have to deal with three different aspects of troubleshooting permissions - ownership, Unix file permissions and SELinux permissions? Turns out, as long as you have at least one file around that already has the correct owner, permissions and SELinux contexts you can rapidly clone everything with the --reference flag - a trick that took me way too...
Ever have that moment where you’re working on your SELinux enabled webserver and you’ve put in a fancy new file into /var/www/html and the darn thing just won’t show up properly, even though everything else is working? Then that sinking realization that you have to deal with three different aspects of troubleshooting permissions - ownership, Unix file permissions and SELinux permissions? Turns out, as long as you have at least one file around that already has the correct owner, permissions and SELinux contexts you can rapidly clone everything with the --reference flag - a trick that took me way too...
Recommendations for a Security Education
 Perodically I’ll get asked for recommendations for good resources to get started learning about information security. I’ve written reviews on a number of books, and on a handful of other sources, so I thought I’d collect together some of those, as well as make some new recommendations. Most of these recommendations come from the perspective of someone more on the development side of security than IT. I’ve sorted things out into two broad categories -sources that can provide you with an underpinning for a security education, and sources that are good for on-going education (keeping up with news or learning...
Perodically I’ll get asked for recommendations for good resources to get started learning about information security. I’ve written reviews on a number of books, and on a handful of other sources, so I thought I’d collect together some of those, as well as make some new recommendations. Most of these recommendations come from the perspective of someone more on the development side of security than IT. I’ve sorted things out into two broad categories -sources that can provide you with an underpinning for a security education, and sources that are good for on-going education (keeping up with news or learning...
A Slightly Snarky Overview of Security for Apache Tomcat
 Apache Tomcat crops up a lot, and frequently having been configured by someone without a lot of security background. I’ll spend a little bit of time looking at some of what you can do to improve security at a high level - I won’t be giving step by step instructions, just trying to provide a feel for what the security features can do. For implementation details, you should take a look at the official documentation. Tomcat 7’s security documentation is at Tomcat Security Considerations. For the most part I’m using their documentation as a reference to put together this post,...
Apache Tomcat crops up a lot, and frequently having been configured by someone without a lot of security background. I’ll spend a little bit of time looking at some of what you can do to improve security at a high level - I won’t be giving step by step instructions, just trying to provide a feel for what the security features can do. For implementation details, you should take a look at the official documentation. Tomcat 7’s security documentation is at Tomcat Security Considerations. For the most part I’m using their documentation as a reference to put together this post,...